Information Technology Policy Template
Information Technology Policy Template - Web build strong information security policy: The templates can be customized and used as an outline of an organizational policy, with additional details to. If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. Guidance text appears throughout the document, marked by the word guidance. Web download our information and cyber security policy templates for smbs, startups, and enterprises. Web an ai usage policy is a set of guidelines for a company and its employees that governs how artificial intelligence (ai) technologies can be used. The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. Creating security policies is considered to be the most critical element of an it security program. As technology changes, we publish new policies. Web an information security policy is a set of rules, guidelines, and procedures that outline how an organization should manage, protect, and distribute its information assets. An acceptable use policy (aup) is a document outlining rules and guidelines for using an organization's it resources, including networks, devices, and software. Definitions of confidential data and the importance of its protection. Every company that uses information technology (it) should have an it security policy. Information technology office, chief officer [officer.firstname] [officer.lastname]. Web an ai usage policy is a. Web an ai usage policy is a set of guidelines for a company and its employees that governs how artificial intelligence (ai) technologies can be used. Web cyber security policy template. Audit logging and monitoring policy. If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. Web this company. 71 votes with an average rating of 2.6. Creating security policies is considered to be the most critical element of an it security program. Sans.org/), the state of new york, and the state of california. Web 100+ critical it policies every company needs, ready for download. Our list includes policy templates for acceptable use policy, data breach response policy, password. Web below, learn about why policies are critical for security, the common types of cybersecurity policies, how to prepare an it security policy and the components of a security policy. From remote work and social media to ergonomics and encryption, techrepublic premium, zdnet's sibling site, has dozens of. Web this company cyber security policy template is ready to be tailored. From remote work and social media to ergonomics and encryption, techrepublic premium, zdnet's sibling site, has dozens of. Implementing an ai usage policy isn’t just a procedural step; The templates can be customized and used as an outline of an organizational policy, with additional details to. Web the it policy of a company defines the rules, regulations, and guidelines for. These are free to use and fully customizable to your company's it security practices. Web an ai usage policy is a set of guidelines for a company and its employees that governs how artificial intelligence (ai) technologies can be used. Web cyber security policy template. Web this template for an it policy and procedures manual is made up of example. Web below, learn about why policies are critical for security, the common types of cybersecurity policies, how to prepare an it security policy and the components of a security policy. It encompasses key areas such as purpose and objectives, authority, scope, organizational security management, functional responsibilities, and much more. Web choose from our 33 customizable it security policy templates, each. Web an ai usage policy is a set of guidelines for a company and its employees that governs how artificial intelligence (ai) technologies can be used. This cyber security policy should include: As technology changes, we publish new policies. Web cyber security policy template. Web 100+ critical it policies every company needs, ready for download. An it policy template helps you create a set of rules that tells your employees how they should handle information technology in your company. As technology changes, we publish new policies. It defines acceptable and prohibited behaviors, aiming to protect assets, ensure security, and maintain a productive work environment. Use the table of contents below to jump to the template. Web an ai usage policy is a set of guidelines for a company and its employees that governs how artificial intelligence (ai) technologies can be used. Audit logging and monitoring policy. Web sans has developed a set of information security policy templates. Different it policy templates focus on different use cases. Web download our information and cyber security policy templates. Web below, learn about why policies are critical for security, the common types of cybersecurity policies, how to prepare an it security policy and the components of a security policy. Web the it policy of a company defines the rules, regulations, and guidelines for the proper usage, security, and maintenance of the company’s technological assets including the computers, mobile devices, servers, internet, applications, etc. Want to protect yourself from emerging cyber threats? Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web choose from our 33 customizable it security policy templates, each ready for your logo and specific mapping requirements: Equal employment opportunity commission (eeoc) published final guidance on harassment in the workplace, “enforcement guidance on harassment in the workplace.”by providing this resource on the legal standards and employer liability applicable to harassment claims under the federal employment. Web each it policy template includes an example word document, which you may download for free and modify for your own use. Web build strong information security policy: It typically details ethical use, managing risks, and complying with legal and regulatory standards. Sans.org/), the state of new york, and the state of california. An acceptable use policy (aup) is a document outlining rules and guidelines for using an organization's it resources, including networks, devices, and software. It encompasses key areas such as purpose and objectives, authority, scope, organizational security management, functional responsibilities, and much more. Web information technology security policies are a set of written practices and procedures that all employees must follow to ensure the confidentiality, integrity, and availability of data and resources. Web this template for an it policy and procedures manual is made up of example topics. For example, you would need to come up with policies to regulate your company’s security and information technology so that you could do your work properly. As technology changes, we publish new policies.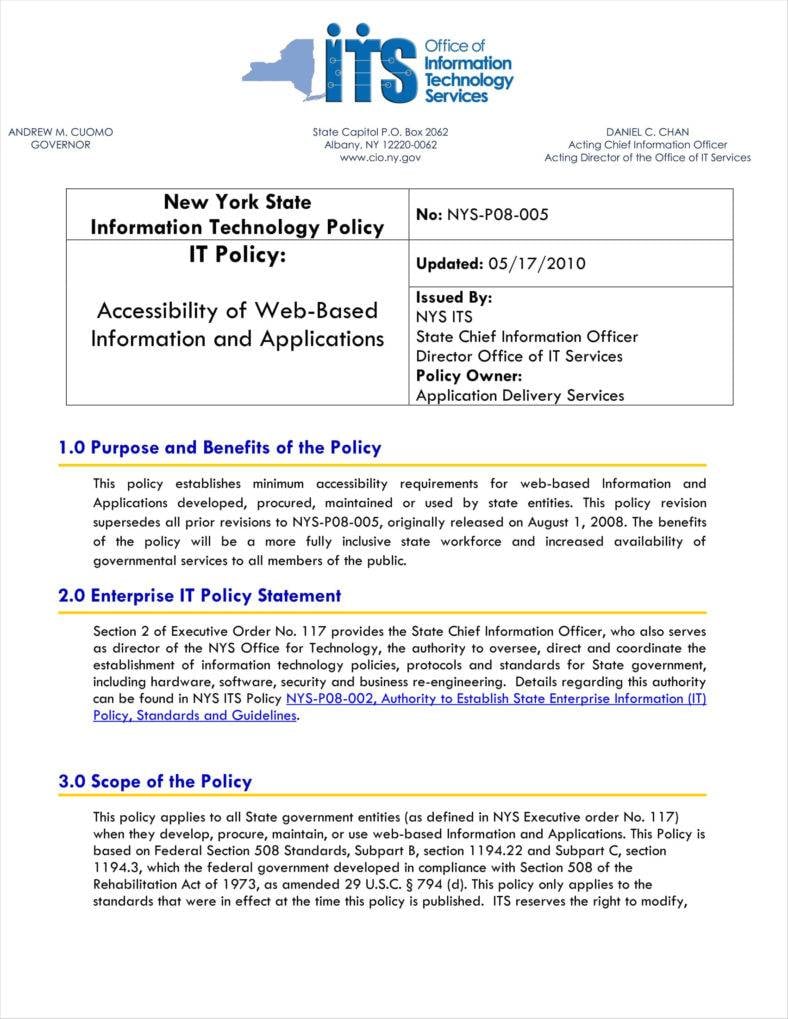
18+ IT Policy Templates PDF, DOC Format Download

Bank Information Technology Policy Template Package

Pin on 100+ Examples Online Form Templates

Information Technology Policy Template Best Of asset List Example Fixed

Usage Policy Template

Information Technology Policy Template Elegant Data Governance Plan

Information Technology Policy Template Awesome Here to Download This

Information Technology Policy Template Luxury Template Policies and

Information Technology Policy Template Shooters Journal

Information Technology Policy Template Best Of It Security Policy
If You Have Any Kind Of Organization, Then You Might Have To Develop Your Own Policies Regarding How The Organization Operates.
Best Of All, We’re Constantly Adding To Our Policy Library.
Our List Includes Policy Templates For Acceptable Use Policy, Data Breach Response Policy, Password Protection Policy And More.
Web Download Our Information And Cyber Security Policy Templates For Smbs, Startups, And Enterprises.
Related Post: