Security Log Template
Security Log Template - What is a daily patrol log. Web managing device deployment templates. Aside from the security incident report, security officers are also tasked with creating and maintaining a security incident log. It can also be used for routine log review. Enter your name, date, shift start. Web how to create a company password policy, with template. Included in the security shift report template. The first method, which triggers a file access log entry, involves opening. This easy to use template will help you figure out what initial steps you need to take to properly start. Whether you’re a security guard, building manager, or security firm owner, use. It can also be used for routine log review. Web managing device deployment templates. Web use the security shift report template or go digital? Web both actions, varonis noted, involve file downloads but neither are logged as such. Log files are a key part of any iso 27001 compliant information security management system (isms). Create a deployment template from a reference device; Web this cheat sheet presents a checklist for reviewing critical logs when responding to a security incident. Web 5.1 network access control. Security shift report (watermarked) by 1st reporting. It can also be used for routine log review. Web the template below demonstrates the information required of an outstanding daily activity report for security guards. Aside from the security incident report, security officers are also tasked with creating and maintaining a security incident log. Web the legacy versions of the compose file reference has moved to the v1 branch of the compose repository. It can also be used. Web this publication seeks to assist organizations in understanding the need for sound computer security log management. Web incident response log template. Web audit log management policy template for cis control 8. Web the template below demonstrates the information required of an outstanding daily activity report for security guards. They play an important role. Get your free copy now! Web an incident log template in it governance is a structured document designed to systematically capture and record details of security incidents, disruptions,. Web use the security shift report template or go digital? Web incident response log template. Enter your name, date, shift start. What is log management and why is it important? This easy to use template will help you figure out what initial steps you need to take to properly start. Web execute and sign your security log template with complete confidence that your document will be safeguarded and that your esignature will be legally binding and admissible in. Security shift report. This easy to use template will help you figure out what initial steps you need to take to properly start. Web a security log form is used by security professionals to record and document security events. Create a deployment template by importing a template file; Create a deployment template from a reference device; Security shift report (watermarked) by 1st reporting. Web download this template! Web the template below demonstrates the information required of an outstanding daily activity report for security guards. Web this publication seeks to assist organizations in understanding the need for sound computer security log management. Whether you’re a security guard, building manager, or security firm owner, use. Web audit log management policy template for cis control 8. Get your free copy now! Web managing device deployment templates. What is a daily patrol log. Enter your name, date, shift start. Create a deployment template from a reference device; Web an incident log template in it governance is a structured document designed to systematically capture and record details of security incidents, disruptions,. Web need for computer security log management—the process for generating, transmitting, storing, analyzing, and disposing of computer security log data. Create a deployment template from a reference device; Get your free copy now! Web execute and sign. Web need for computer security log management—the process for generating, transmitting, storing, analyzing, and disposing of computer security log data. Get your free copy now! Web use the security shift report template or go digital? They play an important role. Web audit log management policy template for cis control 8. Web the legacy versions of the compose file reference has moved to the v1 branch of the compose repository. Log files are a key part of any iso 27001 compliant information security management system (isms). Web download this template! Web an incident log template in it governance is a structured document designed to systematically capture and record details of security incidents, disruptions,. This easy to use template will help you figure out what initial steps you need to take to properly start. The security guard daily report sample is a great way to demonstrate. Web 5.1 network access control. Web how to create a company password policy, with template. Web a security log form is used by security professionals to record and document security events. Whether you’re a security guard, building manager, or security firm owner, use. Web this cheat sheet presents a checklist for reviewing critical logs when responding to a security incident.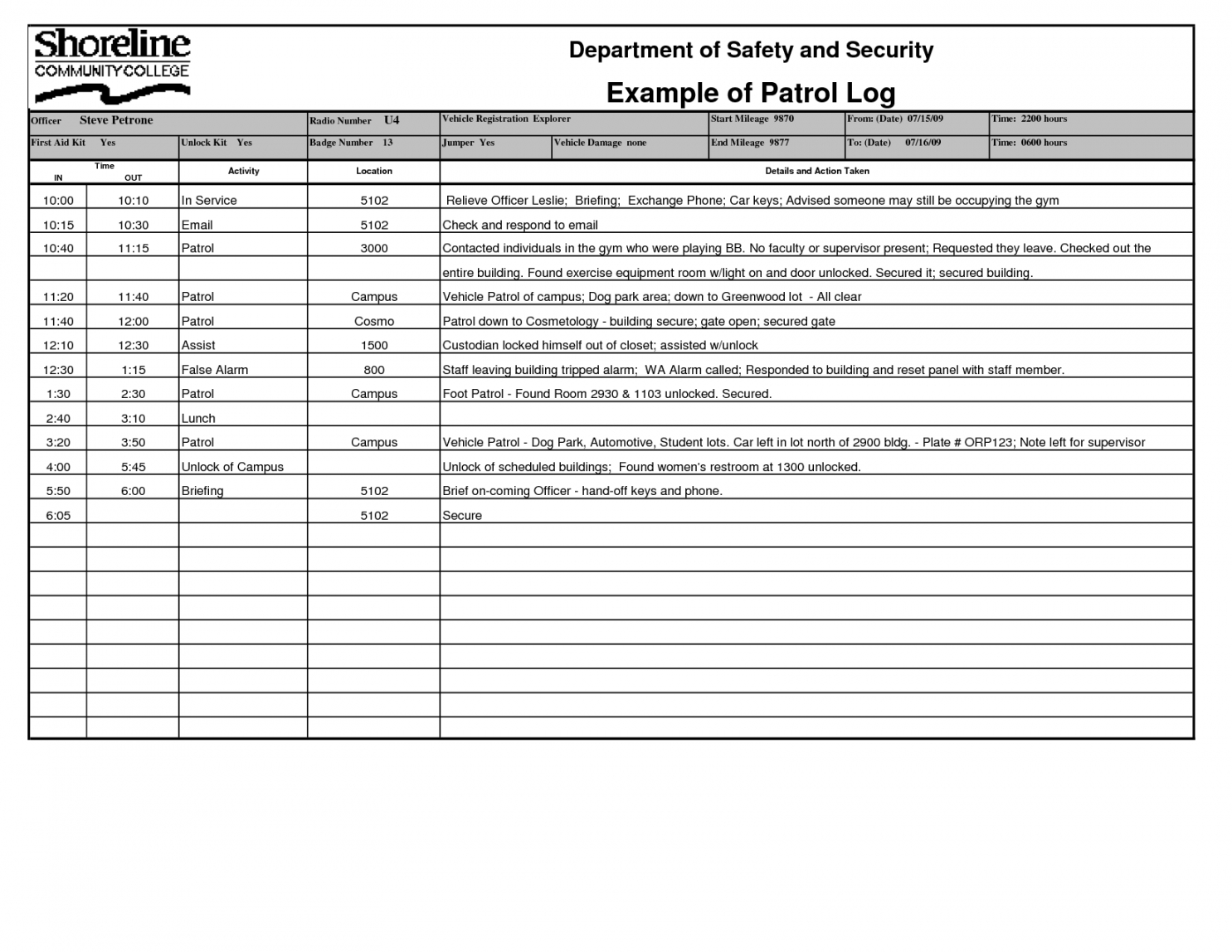
Security Patrol Checklist Template
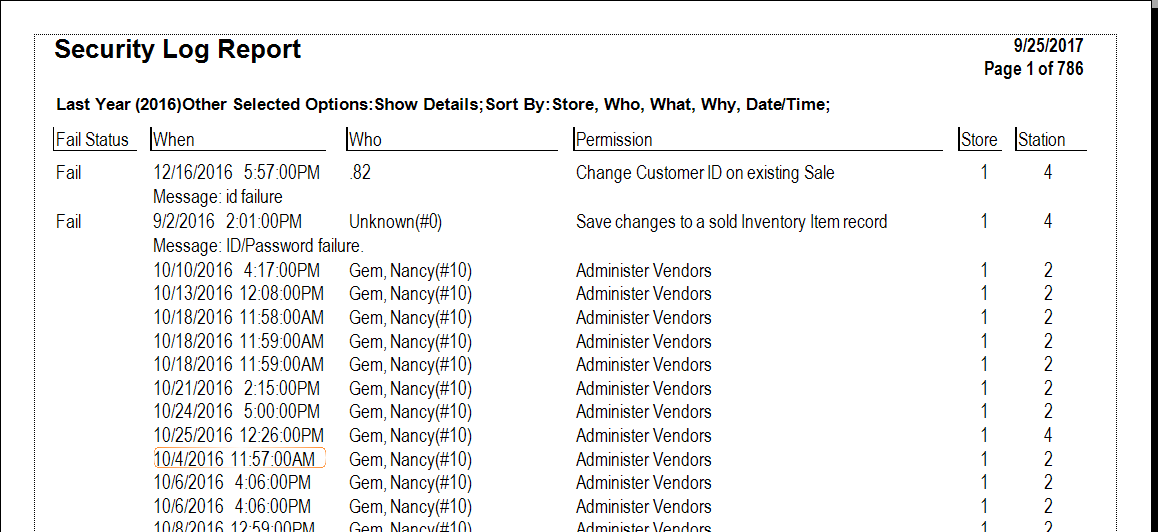
Edge Knowledge Base > Reports > Management Reports > Security Log
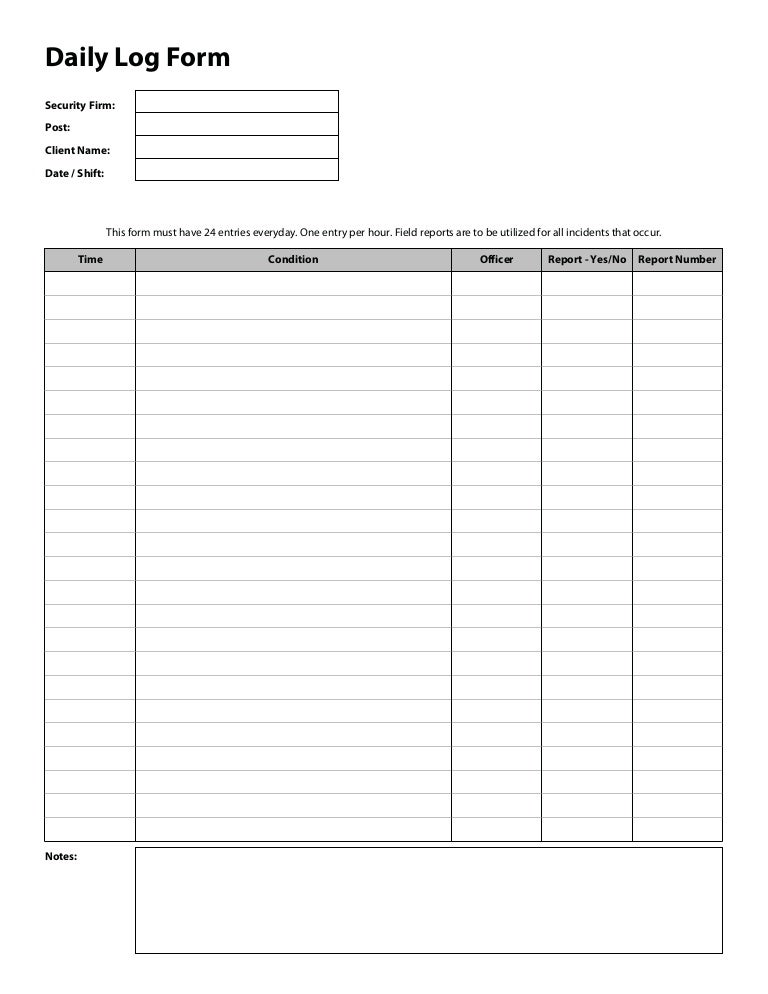
Daily log form__security_guard_use
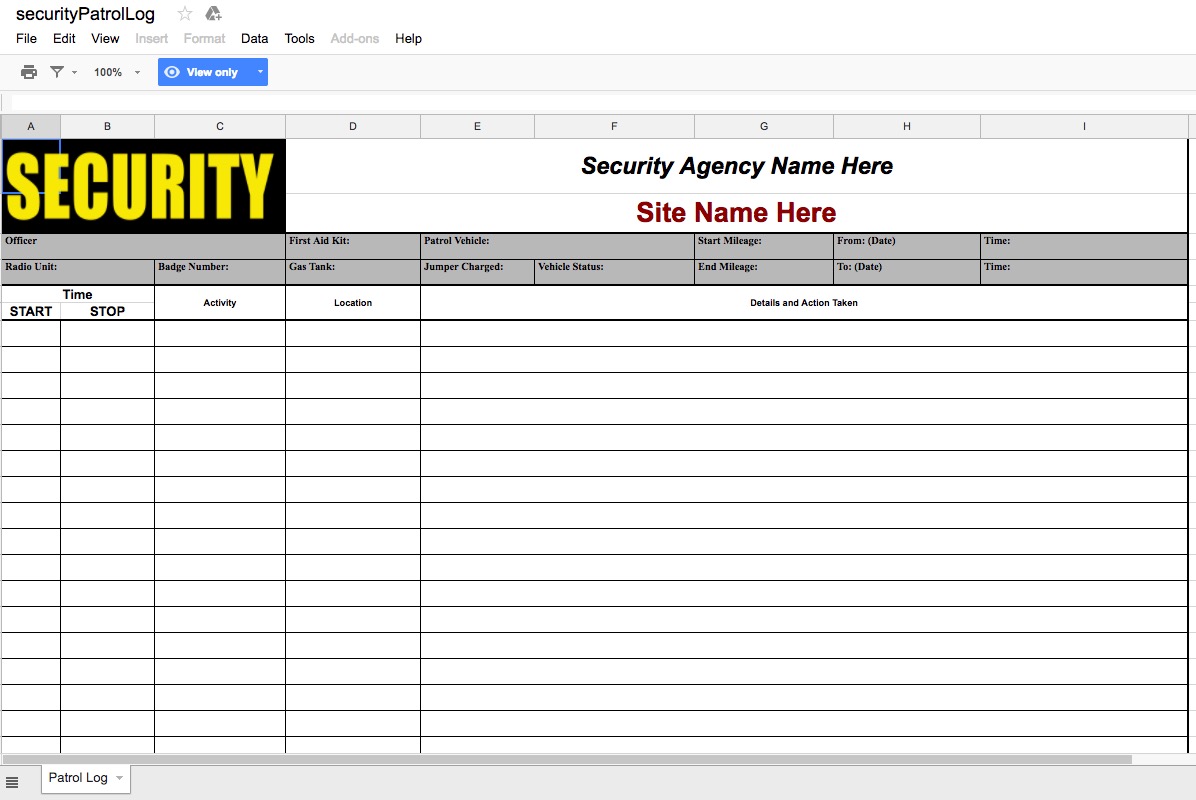
Security Agency Reporting Tip

Daily Activity reports Form Printable Blank PDF Online
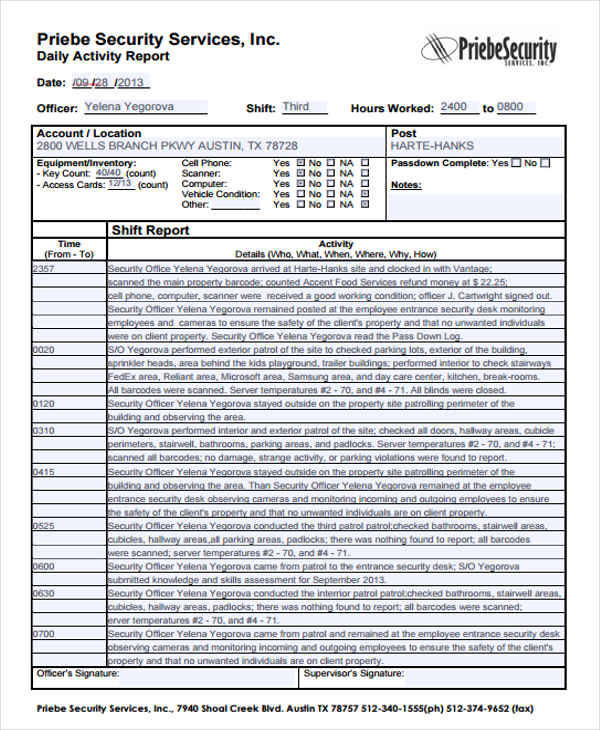
FREE 34+ Daily Log Templates in PDF MS Word
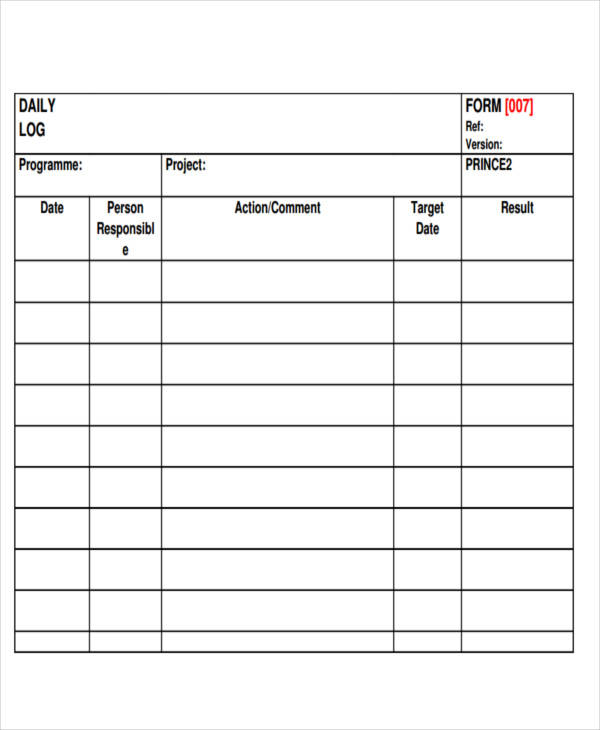
FREE 34+ Daily Log Templates in PDF MS Word
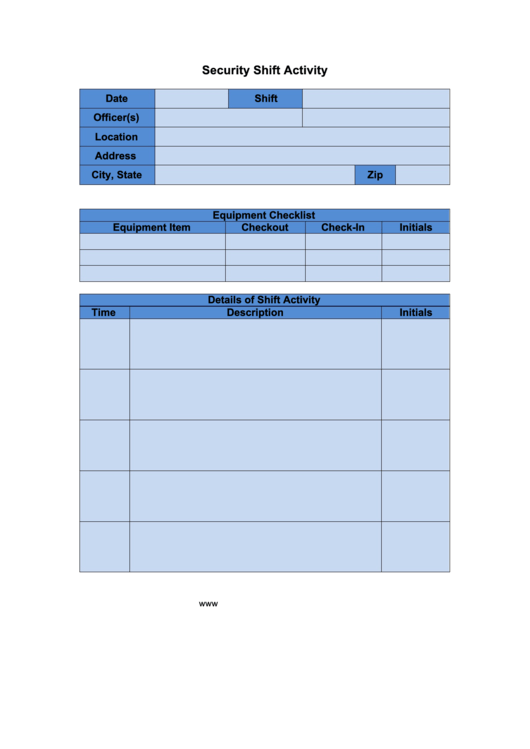
Security Log Book printable pdf download

Security Daily Activity Log Template SMHCSEquipment Usage Daily
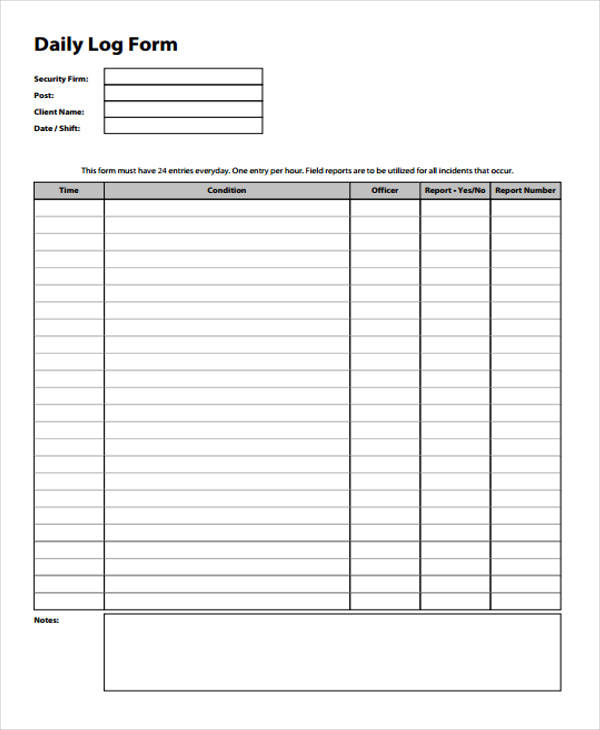
FREE 34+ Daily Log Templates in PDF MS Word
The First Method, Which Triggers A File Access Log Entry, Involves Opening.
Aside From The Security Incident Report, Security Officers Are Also Tasked With Creating And Maintaining A Security Incident Log.
Security Shift Report (Watermarked) By 1St Reporting.
Web Both Actions, Varonis Noted, Involve File Downloads But Neither Are Logged As Such.
Related Post: